Máte pocit, že vás niekto sleduje? Že niekto vie o každom Vašom kroku? Čo ak niekto odpočúva aj tých, ktorí nás majú chrániť? A je vlastne Signal bezpečná Appka? Nuž, V tomto článku sa možno dozviete aj to, čo ste vedieť nechceli. Ale začnem tým, ako som prišiel o všetky ilúzie ja.
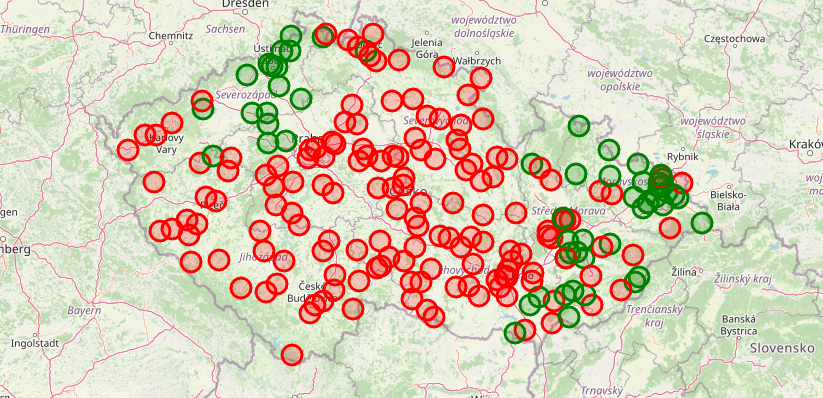
Možno ste pred časom zachytili správu o slabej šifre v protokole TETRA, ktorý po celej Európe používajú rôzne verejné zložky od smetiarov až po mestské polície na komunikáciu. Väčšina z týchto zložiek donedávna využívala komerčnú verziu protokolu s blokovou šifrou TEA1, ktorá bola v 90. rokoch úmyselne oslabená tak, aby sa dala rýchlo a jednoducho prelomiť – kvôli možnosti technológiu exportovať. Snáď nikoho neprekvapuje, že nútené pridávanie backdoorov do produktov funguje ako bežná prax nielen v Číne a v Spojených Štátoch, ale aj v Európe.
Ak implementáciu niekto odflákne, dá sa klesnúť ešte hlbšie – pred 10 rokmi totiž väčšina TETRA sietí v Česku mala šifrovanie úplne vypnuté…
Continue reading “Brno Ako na Dlani a Anjeli Strážni z Temu”

![[Aktualizované] Uniknutý firmvér z Ruska – Zakážu nám Flippera?](https://santomet.eu/wp-content/uploads/2025/04/flipper-flip-scaled.jpg)